USB flash drives
are great BUT it doesn’t come with any security
at all. USB flash drives are small and can be easily misplaced or
stolen. In that case, all our pendrive content is open for others. We
can play safe by not letting other people get our data in a pendrive by
encrypting the drive.
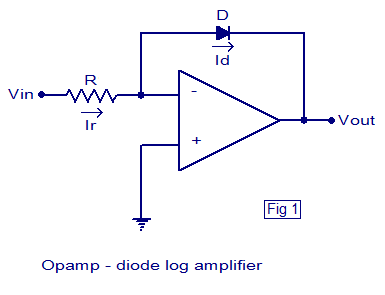
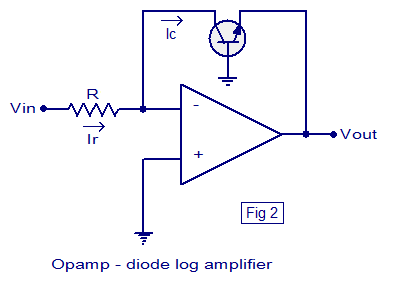
USB Flash Security is a security software that protects data in a USB flash drive by a password. It also offers a better way of protecting files which is that it encrypts the whole drive, leaving only a small space to for the unlocker file to sit in. If someone formats the drive, your encrypted space and data is still intact and only the unlocker file gets deleted which can be easily restored from the program on your computer.
Here’s a short walk-through on how easy it is to use USB Flash Security. After installation and run the shortcut, here’s what USB Flash Security looks like. It will automatically detect your flash drive when you insert one. All you need to do is click the Install button.
USB Flash Security is a security software that protects data in a USB flash drive by a password. It also offers a better way of protecting files which is that it encrypts the whole drive, leaving only a small space to for the unlocker file to sit in. If someone formats the drive, your encrypted space and data is still intact and only the unlocker file gets deleted which can be easily restored from the program on your computer.
Here’s a short walk-through on how easy it is to use USB Flash Security. After installation and run the shortcut, here’s what USB Flash Security looks like. It will automatically detect your flash drive when you insert one. All you need to do is click the Install button.
Then you will be prompted to enter a password and the optional hint to remind you of your password if you forget.
After encrypting your USB flash drive, you can only find 2 files (autorun.inf and UsbEnter.exe) in your drive. Run UsbEnter.exe, enter your password and within a few quick seconds you’ll have access to the encrypted space for you to save, edit or delete files.
When you’re done, simply unplug or eject your flash drive and it will be automatically locked.
If you check the encrypted USB flash drive space, it’s only 476KB on my 8GB drive. That explains why even after formatting the drive the encrypted data is untouched as it only formats the 476KB removing the unlocker and autorun file.
Download USB Flash Security from here.